5Ghoul 5Ghoul
https://asset-group.github.io/disclosures/5ghoul/
https://github.com/asset-group/5ghoul-5g-nr-attacks
15th September of 2025: 5Ghoul discovers another 12 new vulnerabilities (ALL 12 with HIGH severity) in baseband modems from a major vendor. Exploits and other details will be released after the embargo.
* 2025 年 9 月 15 日:5Ghoul 发现了该主要供应商基带调制解调器的另外 12 个新漏洞(全部 12 个为高危)。利用代码及其他细节将在禁运期结束后公布。
* 17th June of 2025: The technical approach embodied in 5Ghoul will appear in IEEE TDSC. It is available here.
* 2025 年 6 月 17 日:5Ghoul 所体现的技术方法将发表于 IEEE TDSC。可在此处获取。
* 31st October of 2024: Our 5Ghoul DEFCON32 slides from August 10 are available here.
* 2024 年 10 月 31 日:我们在 8 月 10 日于 DEFCON32 的 5Ghoul 幻灯片可在此处获取。
* 17th May of 2024: We have disclosed two more Mediatek vulnerabilities: CVE-2024-20003 (High severity) and CVE-2024-20004 (Medium severity). More details are provided in Sections 7.11 and 7.12.
* 2024 年 5 月 17 日:我们已披露另外两个联发科漏洞:CVE-2024-20003(高危)和 CVE-2024-20004(中危)。更多细节见第 7.11 节和第 7.12 节。
* 29th December of 2023: After additional severity assessment review from MediaTek, three vulnerabilities have been elevated from Medium to High severity rating. (CVE-2023-32842, CVE-2023-32841 and CVE-2023-32843).
* 2023 年 12 月 29 日:在联发科对严重性评估进行追加审查后,三个漏洞的严重性等级已从中等提升为高危。(CVE-2023-32842、CVE-2023-32841 和 CVE-2023-32843)。
* 15th December of 2023: Our study to estimate the affected smartphones considers phone models that employ the vulnerable 5G modems. However, certain phones may not enable the 5G functionality. We performed further analysis to estimate the number of smartphones that also offer 5G features and amended the study (see Section 4).
* 2023 年 12 月 15 日:我们估算受影响智能手机数量的研究考虑了采用易受攻击 5G 调制解调器的手机型号。然而,某些手机可能未启用 5G 功能。我们进行了进一步分析以估算同时提供 5G 功能的智能手机数量,并对研究进行了修订(见第 4 节)。
* 7th December of 2023: As of today, we disclose a total of 14 vulnerabilities (10 CVEs), of which 10 affect commercial off-the-shelf (COTS) edge devices employing 5G modems from Qualcomm and MediaTek. At least two other vulnerabilities are not disclosed yet due to confidentiality. This page will continue to be updated as our experiment progresses and the embargo is lifted. For more details on each disclosed vulnerability, please refer to Section 7. Feel free to contact us via contact@5ghoul.com.
* 2023 年 12 月 7 日:截至今日,我们披露了共 14 个漏洞(10 个 CVE),其中 10 个影响使用高通和联发科 5G 调制解调器的商用现成(COTS)边缘设备。至少另外两个漏洞由于保密原因尚未披露。随着我们的实验推进和禁运期解除,本页面将继续更新。有关每个已披露漏洞的更多详细信息,请参阅第 7 节。如需联系,请发邮件至 contact@5ghoul.com。
* 4th December of 2023: Following a responsible disclosure period, the December security bulletin of MediaTek includes details of all MediaTek Chipsets affected by 5Ghoul vulnerabilities [10]. Likewise, all Qualcomm Chipsets affected by 5Ghoul vulnerabilities are detailed in December security bulletin of Qualcomm [13].
* 2023 年 12 月 4 日:在负责任披露期后,联发科的 12 月安全公告包含了受 5Ghoul 漏洞影响的所有联发科芯片组的详细信息[10]。同样,受 5Ghoul 漏洞影响的所有高通芯片组也在高通的 12 月安全公告中有详细说明[13]。
Sni5Gect https://asset-group.github.io/Sni5Gect-5GNR-sniffing-and-exploitation/#/
https://github.com/asset-group/Sni5Gect-5GNR-sniffing-and-exploitation
A framework for 5G NR Sniffing and Injection
A framework for 5G NR sniffing and exploitation用于 5G NR 嗅探与利用的框架
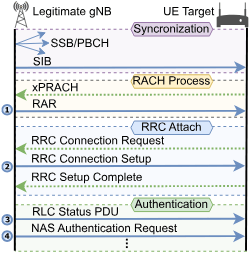
Sni5Gect (Sniffing 5G Inject) is a framework designed to sniff unencrypted messages sent between the base station and the UE, and inject messages to target User Equipment (UE) over-the-air at specific states of 5G NR communication. It can be used to carry out attacks such as crashing the UE modem, downgrading to earlier generations of networks, fingerprinting, or authentication bypass.
Sni5Gect(Sniffing 5G Inject)是一个用于嗅探基站与用户设备(UE)之间传输的未加密消息,并在 5G NR 通信的特定状态下对目标用户设备(UE)进行空中注入消息的框架。它可被用于执行诸如使 UE 基带崩溃、降级到早期代网络、指纹识别或绕过认证等攻击。
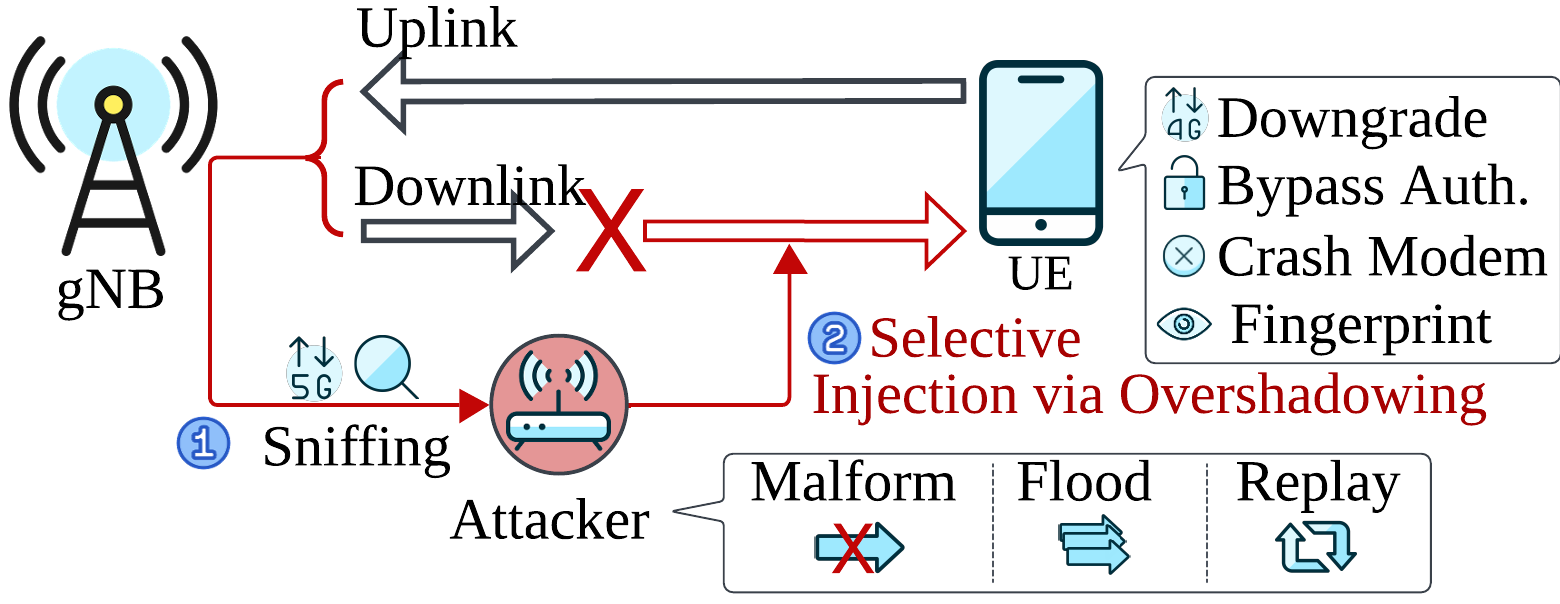
Sni5Gect is a framework for sniffing unencrypted 5G messages and injecting custom packets into the over-the-air communication between a base station and a User Equipment (UE). It can be used for security research to perform attacks like crashing UE modems, network downgrades, fingerprinting, and auth bypass. The tool has been tested with commercial UEs (smartphones, modems) and srsRAN/Effnet base stations.
Sni5Gect 是一个用于嗅探未加密的 5G 消息并向基站与用户设备(UE)之间的空中通信注入自定义数据包的框架。它可用于安全研究,执行诸如使 UE 调制解调器崩溃、网络降级、指纹识别和认证绕过等攻击。该工具已在商用 UE(智能手机、调制解调器)和 srsRAN/Effnet 基站上进行了测试。
Core Features 核心功能
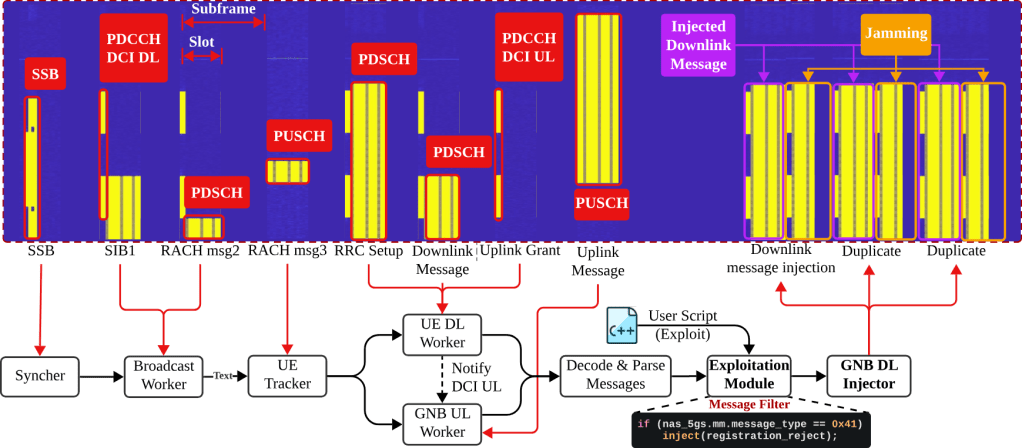
- 🔎 Sniff: Capture 5G MAC-NR unencrypted messages between the base station and UE.
🔎 嗅探:捕获基站与 UE 之间的 5G MAC-NR 未加密消息。 - 💉 Inject: Send arbitrary MAC-NR messages to a target UE at specific communication states.
💉 注入:在特定通信状态下向目标用户设备发送任意 MAC-NR 消息。
Example Use Cases 示例用例
- 💥 Crash UE modems.
💥 使用户设备基带崩溃。 - 📉 Downgrade attacks (5G to 4G).
📉 降级攻击(从 5G 到 4G)。 - 👆 Device Fingerprinting.
👆 设备指纹识别。 - 👹 Anomaly Detection. 👹 异常检测。
Sni5Gect artifacts paper received badges Available, Functional and Reproduced in the 34th USENIX Security Symposium. Artifacts PDF available here
Sni5Gect 工件论文在第 34 届 USENIX 安全研讨会上获得了 Available、Functional 和 Reproduced 徽章。工件 PDF 可在此处获取
Overview 概述

v2.0 – FDD Support (17th September 2025)
v2.0 – FDD 支持(2025 年 9 月 17 日)
This release expands Sni5Gect with new capabilities:
此版本为 Sni5Gect 增加了新的功能:
- Dual-channel FDD support: Receive and process IQ samples from two channels simultaneously using SDRs with dual RX chains.
双通道 FDD 支持:使用具有双接收链的 SDR 同时接收并处理来自两个信道的 IQ 采样。 - Unified codebase for 15 kHz and 30 kHz subcarrier spacing without recompilation.
统一代码库,支持 15 kHz 和 30 kHz 子载波间隔,无需重新编译。 - Expanded testing with the following setups:
扩展的测试,包含以下设置:- Frequency Bands: 频段:
- TDD: n78, n41 TDD:n78、n41
- FDD: n3 FDD:n3
- Frequency: 3427.5 MHz, 2550.15 MHz, 1865.0 MHz
频率:3427.5 MHz、2550.15 MHz、1865.0 MHz - Subcarrier Spacing: 30 kHz, 15 KHz
子载波间隔:30 kHz、15 kHz
- Frequency Bands: 频段:
Note: Since FDD uses separate frequencies for downlink and uplink, an SDR with two RF front-ends (e.g., USRP X310) is required to capture IQ samples from both frequencies simultaneously (otherwise Sni5Gect is only capable of sniffing the downlink channel). A GPSDO is strongly recommended for frequency synchronization; without it, manual calibration may be necessary.
注意:由于 FDD 在下行链路和上行链路使用不同频率,需使用具有两个射频前端的 SDR(例如 USRP X310)来同时捕获两个频率的 IQ 样本(否则 Sni5Gect 仅能嗅探下行信道)。强烈建议使用 GPSDO 进行频率同步;若无 GPSDO,可能需要手动校准。
v1.0 – Initial Release (26th August 2025)
v1.0 – 初始发布(2025 年 8 月 26 日)
The first release of Sni5Gect, supports TDD bands with a 30 kHz subcarrier spacing. Tested configurations:
Sni5Gect 的第一个版本,支持具有 30 kHz 子载波间隔的 TDD 频段。已测试配置:
- Frequency Bands: n78, n41 (TDD)
频段:n78、n41(TDD) - Frequency: 3427.5 MHz, 2550.15 MHz
频率:3427.5 MHz,2550.15 MHz - Subcarrier Spacing: 30 kHz
子载波间隔:30 kHz - Bandwidth: 20–50 MHz 带宽:20–50 MHz
- MIMO Configuration: Single-input single-output (SISO)
MIMO 配置:单输入单输出(SISO) - Distance: 0 meter to up to 20 meters (with amplifier)
距离:0 米到最多 20 米(使用放大器)

Leave a comment